Soon you will be able to control your toaster from the mobile app on your phone.
The cost of the IoT app is decreasing day by day. No wonder we may soon expect that such devices as toasters will be upgraded to fit the requirements of consumers. In the short run, all those who want to make a toast using an app will benefit. Yet it will bring the problem of cybersecurity to a new level.
Though IoT technology promises a real technological revolution 4.0, it’s the technology that requires transformation and enhancement before it is fully secure and efficient. Security is the linchpin of the Internet of Things and the sooner and the better it is solved, the faster we will be able to see real digital transformation in construction, retail, government, and military sectors.
Yet Rome wasn’t built in one day, and IoT devices can’t become secure at once: it’s a long-term consuming process most companies that aim to digitize should go through. To understand the issue of IoT security better, it’s logical to divide it into several categories where security breaches can occur: device layer, data storage layer, network layer, and regulations layer. Let’s have a quick look at all these layers to understand the measures that can be taken to prevent the breach.
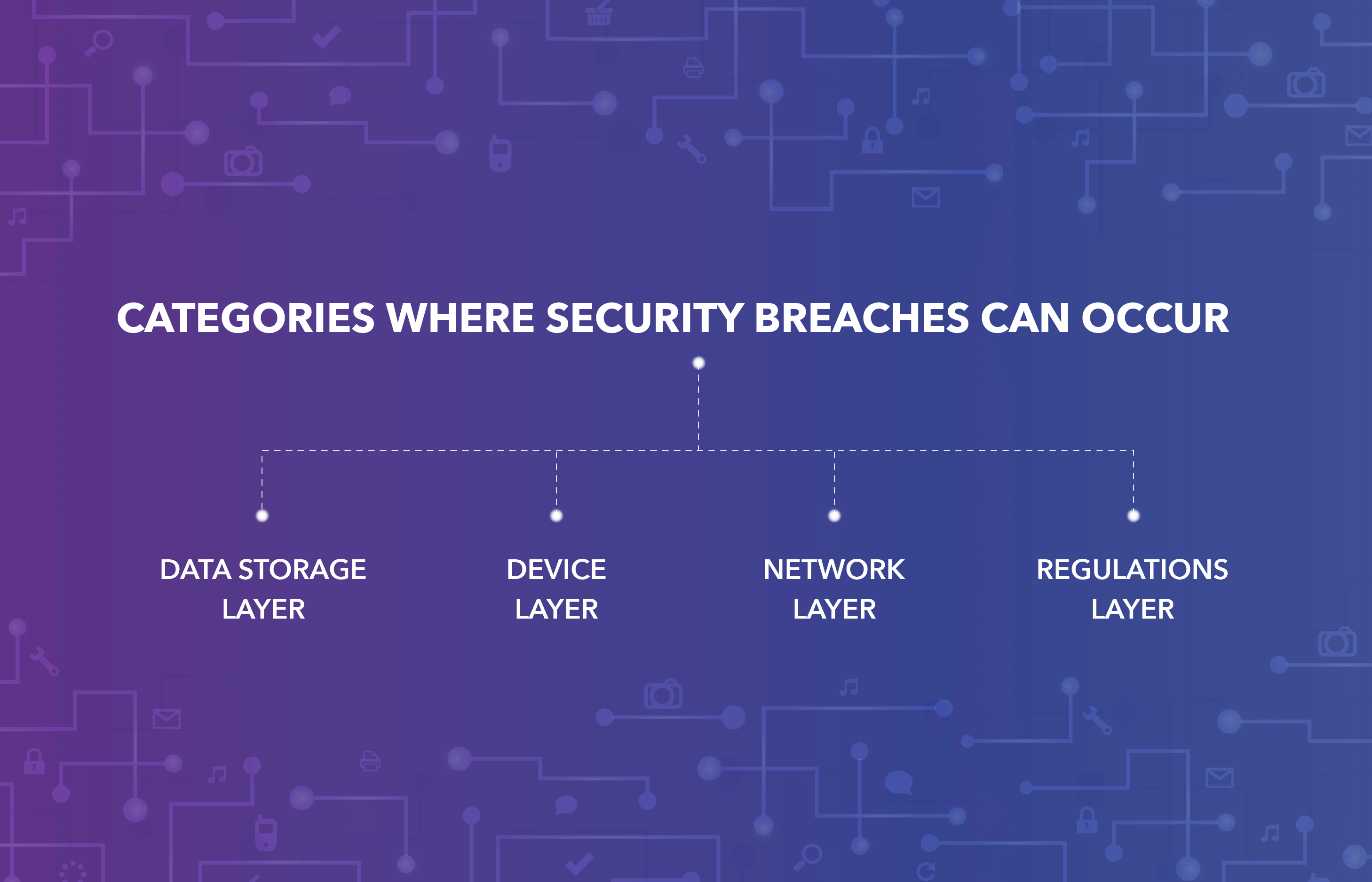
What industries are the most susceptible to the violation of security? The sphere doesn’t actually matter: smart factories can be hacked as often as smart homes. The aftermath is the thing that matters. In some industries, such as the smart home of a single individual, a breach can only cause discomfort, while at the smart factory, it can lead to a disaster.
Devices Security Layer
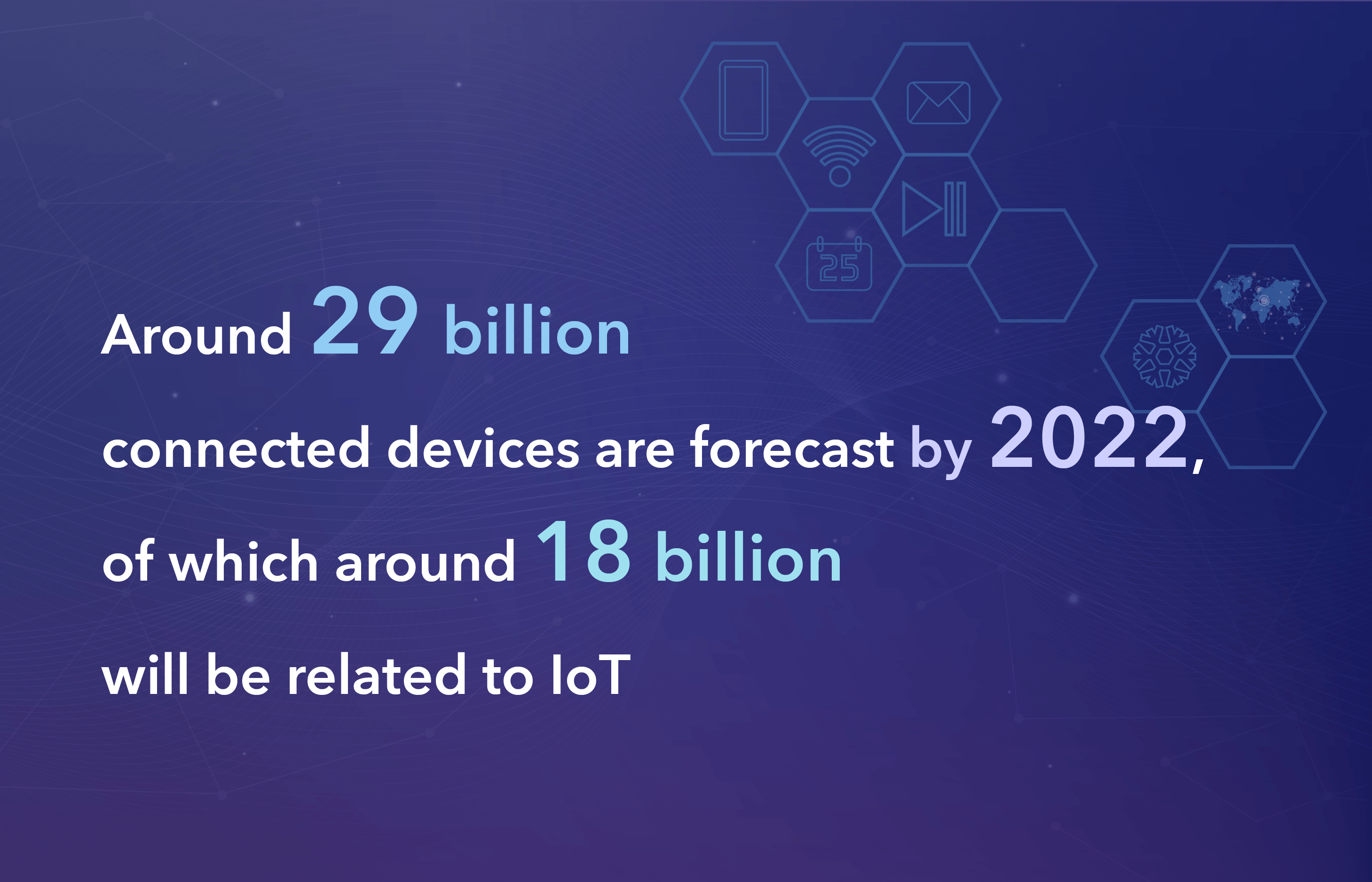
According to Ericsson research, around 29 billion connected devices are forecast by 2022, of which around 18 billion will be related to IoT. It’s not difficult to notice that the number of connected devices is growing exponentially, and today they say that there are more than 20 million gadgets, appliances, and all types of devices capable of smart communication. But in essence, these devices are simple microprocessors ill-equipped to deal with any sort of cyberattack.
Some of the most simple devices, such as humidity sensors, do not have the possibility of advanced security protection. They are not designed for it; therefore, they can easily become the target of cyberattacks. Their resource-constrained nature is connected to their low price and a tendency to forget about them eventually as a result. When the sensor breaks down, users simply throw it away.
For procedures where security has paramount importance, it is crucial to use upgraded devices or prepare them for the attack. So even the most simplistic devices have to be “smart” or otherwise capable of handling security, encryption, authentication, timestamps, caching, proxies, firewalls, connection loss, etc. IoT devices should be capable of working in critical conditions as well.
How to Deal with Ill-Equipped Security Devices?
Сreating advanced IoT devices seems like the most rational solution for dealing with poor security of devices. Alternatively, it’s possible to use edge processing or edge computing which will bring computation and data storage closer to the location where it is required. Some companies upgrade their devices with ML algorithms that permit processing video streams much faster than expected. The choice of IoT security solutions connected to devices vulnerability is diverse, and it’s always possible to choose the one that fits the client perfectly.
Network Security Layer
Network security is a hot topic for IoT security companies. There is a number of network vulnerabilities that should be considered at the stage of development, not after.
Port security is the primary issue: it’s crucial to ensure ongoing port security and take care of disabling port forwarding. Among other network protection methods, there are antimalware and intrusion detection systems that can block unwanted users.
Many devices don’t encrypt messages. Yet encryption has paramount importance for ensuring secure communication between devices. The better the algorithms are, the more chances that the data is protected at rest and in transit. According to IBM, transporting encryption is regarded as the best practice nowadays and using protocols such as TLS.
IoT devices are more difficult to protect because of lower processing power, different connectivity standards, and remote online access as a standard. The access surface of endpoints for attackers is really wide. Utilizing separate networks to isolate devices can also be a good approach to establishing confidential communication.
Web/Mobile Application Layer
This is also a vulnerable security point that is nevertheless often neglected. Thus, to prevent any breaches on web/mobile layer. Implementing secure coding principles as well as high-quality testing will lead to the minimization of the number of vulnerabilities.
IoT app design should not only be intuitive, comfortable, and appealing to clients, it must be well thought to prevent security breaches.
Data Breaches Layer
Data breaches, data thefts, and data manipulations are the problems most organizations have to deal with today because data hunters never sleep. Those who have access to information rule the world, they say that is why data security becomes a primary concern. Among all the security layers of IoT devices, data security seems to be the most challenging taking into account an increasing number of data breaches.
Even the most well-prepared governmental organizations are not capable of withstanding data breaches. As a result, irrespective of personal data, corporate data, government data, big data, or IoT data, no individual or entity seems to be immune to data security challenges.
Data storage insecurity is best solved if all the data is stored locally on the servers of the clients. Using advanced cloud storages such as AWS or Azure will also increase the level of security in terms of storage. Organizations can also improve the level of security of cloud storage by IoT applying different Access control policies and cryptography concepts.
Absence of Standards
The absence of industry-accepted standards is also a real obstacle to the creation of secure IoT networks. The problem is that there is no agreed framework that all IoT security companies can rely upon.
Сompanies that have been working in the IoT sector for a long time are pushed to develop their own standards, rules, and regulations and find the best practices. Yet, companies that create industrial IoT solutions are often guided by the standards of the industry leaders. The variety of the standards makes security compliance more difficult and challenging, which is why it is important to rely on the decision of experts that know how to deal with the absence of unified standards.
It’s most effective when IoT developers work together with security specialists so that the first can control the whole process of development from the start and make sure that the proper control measures are implemented.
Conclusions
Building a secure IoT infrastructure is a necessity for all those who want to evolve using the most advanced technological tools. Yet building a secure IoT ecosystem is difficult on all the layers: starting from the gadgets themselves and ending with the regulations and internal training of the team. What makes it even more difficult is the fact that it is necessary to guess the attacks of the future apart from modern attacks and predict how to protect your solution in the future.
However, the majority of companies that have gained substantial experience in IoT development so they think about IoT security on the systems architecture discussion stage of development.





