We live in an increasingly digitized world. Every company and its employees use various software daily and in every aspect of their activities. Unfortunately, software often contains a variety of vulnerabilities. This can occur for different reasons: the applications might have been developed quickly and with a limited budget; no one within the organization is responsible for maintaining the code, or is familiar with the possible vulnerabilities; the affected code can be owned by a third party, so it is impossible to carry out a full assessment of its vulnerabilities, or the software itself is legacy. As a result, information security and the security of products are ignored, thereby exposing users to unnecessary risks of malicious cyber-attacks and illegal penetration. The topic of today’s article – Security Testing.
Intrusion covers a wide range of activities, such as a hacker’s attempts to penetrate the system for fun or disgruntled employees’ revenge on the employer. However, in most cases, the tampering is performed for the purpose of illicit financial gain. Cyber intruders often try to break into enterprise applications that can contain customers’ financial data or credit card details, which, if leaked, can result in a company’s financial and reputational losses. So, ignore application security at your peril.
Security Testing is a Way Out
Fortunately, things are not too bad because these cybersecurity threats can be mitigated. The best way out is to always conduct thorough and comprehensive security testing.
Security testing checks the actual response of the protective mechanisms built into the system to penetration attempts. If these mechanisms fail to properly respond to the attacks, the vulnerabilities discovered can be fixed.
Given unlimited time and resources, a skilled attacker can hack any system. Therefore, a security tester plays the hacker’s role, but on legal grounds. He/she is allowed to do anything:
- Attempt to obtain passwords using external facilities;
- Attack the system with the help of special utilities analyzing the system security;
- Suppress, or overwhelm the system (hoping for it to stop serving other clients), thus looking for a “hole” in the security system;
- Purposefully introduce errors in the hope of penetrating the system during its recovery;
- View unclassified data to find the key to enter the system.
OWASP Top 10
Of course, security testing requires a comprehensive approach. So, it is desirable to conduct it based on clearly defined standards. As a guideline, one can use the OWASP Top 10 Most Critical Web Application Security Risks (hereinafter “OWASP Top 10”), which is the list of top web application vulnerabilities, the most critical security risks collectively identified by many of the world’s leading information security experts.
This OWASP Top 10 list is based on both the frequency of the attacks and the magnitude of their impact on businesses (see Table 1).
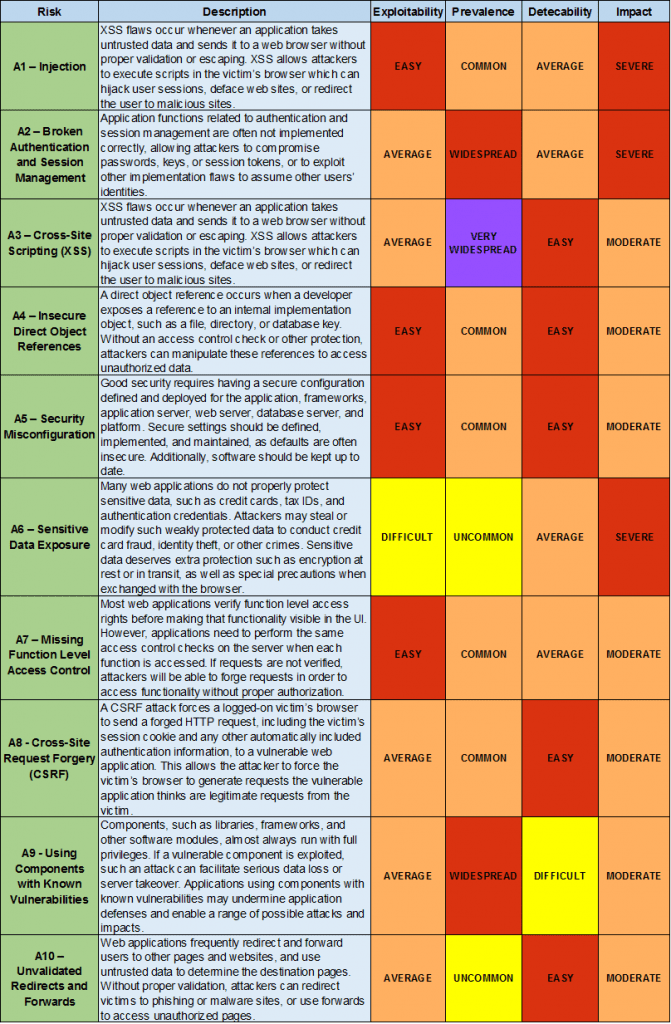
While performing security tests on any software, our team focuses on the OWASP Top 10 and other known vulnerability lists.
Which Resources Are Most Exposed to Hacking Attacks?
Statistically, the banking industry is the leader in the number of systems with high-risk vulnerabilities. Further, there is a high percentage of web applications exposed to critically dangerous vulnerabilities in the fields of telecommunications, information technologies, and industry, followed by eCommerce.
Other industries that are highly affected by vulnerabilities of all kinds include financial services companies (e.g., companies engaged in enterprise taxation, business activities, stock market trading, etc.); public health enterprises, insurance companies, development bureaus, pharmaceutical companies, cosmetic companies, etc.; companies that develop high-tech equipment (dealing with the protection of patents, designs, etc.); law firms (which possess internal customer information protected by lawyer-client privilege); and the gambling industry, especially online casinos (which need to give special protection to user accounts).
The Most Common Security Vulnerabilities (Our Observations)
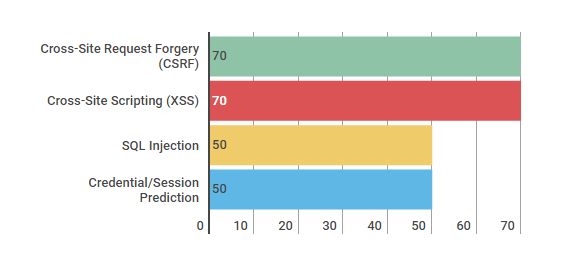
Softengi’s security testing experience shows that almost 70% of all resources are subject to critical vulnerabilities.
The most commonplace vulnerabilities are Cross-Site Request Forgery (CSRF) and Cross-Site Scripting (XSS) found in the code of almost 70% of the web applications analyzed. By exploiting the latter, an intruder can make the application send untrusted data to a victim’s web browser without proper validation, thus allowing the attacker to execute scripts in this browser, which can hijack user sessions and redirect the user to malicious or deface websites.
As practice shows, the implementation of SQL Operators (SQL Injection) is still among the OWASP Top 10 and vulnerabilities revealed by our QA team. In recent years, this defect has been one of the most common threats and has been detected in almost half of all web applications. Using this vulnerability, an attacker can gain unauthorized access to the DBMS and, consequently, to the confidential information stored in the application database. If the DBMS user account has the appropriate privileges within the operating system, an attacker can expand the attack up to getting complete control over the server.
Also, 50% of all the websites tested by our engineers had vulnerabilities associated with using predictable values of user and session IDs (Credential/Session Prediction).
Chart 1. The Most Common Security Vulnerabilities
According to Gartner, Inc., over 70% of security vulnerabilities exist at the application layer, not the network layer, and 75% of security breaches happen at the application layer.
How to Raise the Level of Product Safety With Security Testing?
To avoid critical vulnerabilities occurring in the software, we recommend pursuing the following actions:
- Introduce secure application development practices in the company;
- Train employees on safety methodologies and the rules of software development;
- Have architects or security specialists analyze the code;
- Ensure that acceptance and security testing (at least using automated tools) is carried out;
- Modify the code within the shortest possible time to fix any revealed defects;
- Use network firewalls;
- Continuously monitor the network and requests.
Real Case Study – Security Testing
The Softengi QA Department has performed the security testing of a governmental organization’s website.
To detect vulnerabilities, our specialists used the following methods/approaches:
- Dynamic Security Scanning (DSS)
- Automated Ethical Hack (AEH)
- Manual Ethical Hack (MEH)
As a result of the conducted testing, our team identified vulnerabilities of the various levels of risk:
- Broken Authentication – High Risk
- Cross-Site Scripting (XSS) – High Risk
- SQL Injection – Critical Risk
Most importantly, the website was based on an outdated framework version and had long been known on the Internet for its vulnerabilities.
Igor Sharinsky, Head of the Softengi QA Department: “After finishing the testing procedure, we prepared a detailed report that contained information about the potential vulnerabilities and provided recommendations on how to address them. The primary suggestions were to migrate the website to the new version of the framework, block access to the database, and prevent the possibility of intercepting email addresses of users in the process of their registration.”
After the respective changes were introduced to the website infrastructure and code, its security level significantly increased.
If you are interested in scheduling a meeting with Igor Sharinsky, Head of Softengi QA Department, to find out more about Softengi testing projects, or just to have an initial consultation, please send an email to [email protected].